Virtual Private Cloud (VPC) and Virtual Private Cloud Peering, breaking it down in a clear, practical way with examples and diagrams.
Virtual Private Cloud (VPC):
Imagine you're building a digital fortress, a secure space in the vast landscape of the internet where you can run your applications and store your data. That's essentially what a Virtual Private Cloud (VPC) is – a virtual network environment that's isolated from other networks, providing a secure and controlled space for your resources in the cloud.
Key Components of a VPC:
Subnets: Just like different districts within a city, subnets divide your VPC into smaller, manageable parts. Each subnet has its own range of IP addresses and can be configured with its own settings and access controls.
Route Tables: Think of route tables as maps that guide traffic within your VPC. They determine where data packets should go based on their destination, directing them to the appropriate subnets or external networks.
Security Groups: Security groups act as digital bouncers, controlling who can enter and exit your VPC. You can configure rules to allow or deny traffic based on protocols, ports, and IP addresses, ensuring that only authorized connections are permitted.
Network Access Control Lists (ACLs): ACLs provide an additional layer of security by filtering traffic at the subnet level. Similar to security groups, they allow you to define rules for inbound and outbound traffic, protecting your VPC from unauthorized access.
Real-Time Experience:
Let's say you're running an e-commerce website on AWS (Amazon Web Services), and you want to set up a VPC to host your application servers, databases, and other resources securely.
Creating a VPC: You start by creating a VPC with a unique CIDR (Classless Inter-Domain Routing) block, defining the range of IP addresses for your virtual network. This VPC will serve as the foundation for your digital infrastructure.
Subnet Configuration: Within your VPC, you create subnets to organize your resources. For example, you might have a public subnet for web servers accessible from the internet and private subnets for database servers that need to be isolated.
Security Settings: Next, you configure security groups and network ACLs to control traffic flow and enforce security policies. You might set up rules to allow HTTP and HTTPS traffic to your web servers while blocking unauthorized access to your database servers.
Route Tables: You configure route tables to ensure proper routing of traffic within your VPC and to external networks. For instance, you might create a route that directs internet-bound traffic to a NAT (Network Address Translation) gateway for outbound communication.
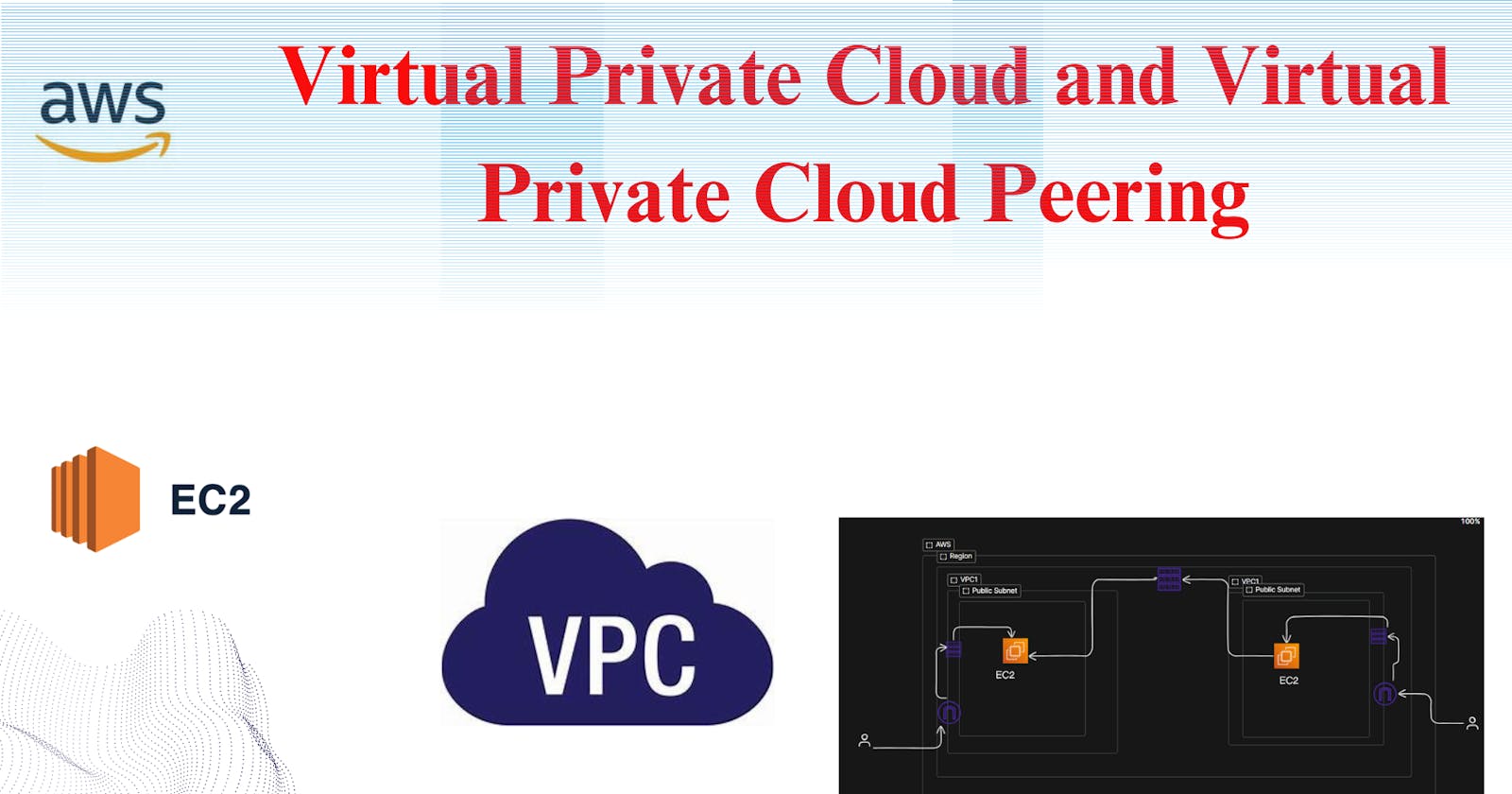
Virtual Private Cloud Peering (VPC Peering):
Now, let's take your digital fortress to the next level with VPC peering. Imagine you have multiple VPCs across different regions or AWS accounts, and you want them to communicate with each other seamlessly.
Benefits of VPC Peering:
Interconnectivity: VPC peering allows VPCs to communicate with each other as if they were part of the same network, enabling seamless data exchange between resources.
Simplicity: Unlike traditional networking solutions that require complex configurations, VPC peering simplifies inter-VPC communication with a straightforward setup process.
Cost-Effectiveness: By leveraging VPC peering, you can avoid data transfer charges associated with traffic flowing between VPCs within the same AWS region.
Real-Time Experience:
Let's extend the scenario of your e-commerce website. Suppose you decide to expand your operations to include a separate VPC for order processing and inventory management, located in a different AWS region.
Setting up VPC Peering: You initiate a VPC peering connection between your existing VPC (hosting the website) and the new VPC (handling order processing). This establishes a direct, private link between the two virtual networks.
Configuring Route Tables: Once the VPC peering connection is established, you update the route tables in both VPCs to enable traffic routing between them. This allows your website servers to communicate with the order processing systems seamlessly.
Security Considerations: While VPC peering simplifies inter-VPC communication, it's essential to consider security implications. You can use security groups and network ACLs to restrict access and ensure that only authorized traffic is allowed between the peered VPCs.
What is Internet Gateways and Route Tables:
Internet Gateways and Route Tables are fundamental components in computer networking, especially within the context of cloud computing and network infrastructure management.
An Internet Gateway serves as the entry and exit point for network traffic between a private network, such as a Virtual Private Cloud (VPC) in cloud computing environments like Amazon Web Services (AWS) or Microsoft Azure, and the public Internet. It acts as a bridge between the internal network and the external world, allowing communication to and from resources within the private network and the broader Internet.
When a network resource within the private network needs to communicate with external resources on the Internet, the traffic is directed to the Internet Gateway. The Internet Gateway then performs the necessary routing functions to ensure that the traffic reaches its intended destination on the Internet and that responses are properly directed back to the originating resource within the private network.
Route Tables, on the other hand, play a crucial role in determining the path that network traffic takes within a network. A Route Table is essentially a set of rules, often in the form of destination-based IP address prefixes and associated next-hop targets, that dictate how traffic should be forwarded within a network.
In the context of cloud computing, each subnet within a VPC typically has an associated Route Table. These Route Tables define how traffic should flow within the VPC, including whether it should be routed locally within the VPC or sent to an Internet Gateway for access to external resources.
When a packet of data arrives at a network device, such as a router or a virtual network interface within a cloud environment, the device consults the appropriate Route Table to determine where to send the packet next based on its destination IP address. If the destination is within the same subnet or VPC, the packet may be routed internally. However, if the destination is outside the local network, the packet is forwarded to the Internet Gateway for further processing and routing toward its final destination on the Internet.
In summary, Internet Gateways and Route Tables are essential components of network infrastructure that enable communication between private networks and the Internet while providing the necessary routing mechanisms to ensure that network traffic reaches its intended destinations efficiently and securely.
Task- Create a 2 VPC Cloud using public network and peering to both VPC:
First you need go to AWS account and go to the VPC.

Now, you need to click Create VPC. Now you need to fill the form, in Resources to create select VPC only , Name tag write VPC1 , no change for IPv4 CIDR block and for IPV4 CIDR write 10.0.0.0/24. we write that is provide 256 IP's. After that no need to change any thing, Just click to Create VPC.


Now we have VPC1.

Now we need to create a public subnets, so go to the subnets section. Click to create subnets.

After that select to VPC1 ID and

we need to enter subnet name that is my-public-subnet, set the Availability zone that is ap-south-1a, by default we have 10.0.0.0/24, So we have have 256 IPs and we need to create IPv4 subnet CIDR block that is 10.0.0.0/26, So we have allocated 64 IPs in public subnets.

After that no change any thing, click to create subnet.

Now we have create public subnet.

Now we need to go create a ec2 machine and add the vpc1. Clear understood by how to create EC2 Maching using with ubuntu:
Go to the AWS Management Console (https://aws.amazon.com/).
Sign in with your AWS account.
Navigate to EC2:
In the AWS Management Console, navigate to the EC2 service.
Launch an Instance:
Click on the "Instances" in the left navigation pane.
Click the "Launch Instances" button.
Choose an Amazon Machine Image (AMI):
In the "Step 1: Choose an Amazon Machine Image (AMI)" section, select an Ubuntu AMI. You can search for "Ubuntu" in the search bar and choose an appropriate version (e.g., Ubuntu Server 20.04 LTS).
Choose an Instance Type:
In the "Step 2: Choose an Instance Type" section, select "t2.micro" as the instance type.
Click "Next: Configure Instance Details."
Network Setting:
In the "Step 3: choose network setting" and click to edit button and add the vpc1 cloud
Configure Security Group:
In the "Step 4: Configure Security Group" section:
Create a new security group or use an existing one.
Add inbound rules to allow HTTP (port 80), HTTPS (port 443), and SSH (port 22) traffic.
after that go to the advance network configuration and add automatically assign secondary IP.
Add Storage:
In the "Step 5: Add Storage" section, you can leave the default storage settings or adjust as needed.
Click "Next: Add Tags."
Add Tags:
In the "Step 6: Add Tags" section, click "Add Tag."
For "Key," enter "Name" and for "Value," enter "Jenkins" (or your preferred name).
Click "Next: Configure Security Group."
Click "Review and Launch."
Review and Launch:
Review your configuration settings.
Click "Launch."
Select Key Pair:
In the key pair dialog, select "Choose an existing key pair" and choose the "minikube" key pair.
Acknowledge that you have access to the private key.
Click "Launch Instances."
View Instances:
Once the instance is launched, you can view it in the EC2 dashboard.
Wait for the instance to reach the "running" state.

Now, go to the VPC and create a Internet gateway.

After that cick to create internet gateway.


Now, After that we need to create a route table so go the the route table section and click to Create route table section.


Now we need to go to Explicit subnet associations in route table and click to edit subnet associations.


Now, we need to go the subnets section add click to edit button.

Now click to edit subnet settings.

After that enable auto-assign public IPv4 address and click to save.

After that go the internet gateway and click to attach to vpc.


Now go to route table, edit to route and attach the internet gateway.


Now go the EC2 Machine and connect the machine.

after that click to connect button.

Now it is connected.

Now, Similarly we will create VPC2 and using vpc-peering1 EC2 machine.

Now we need to pair both the machine. so go to the vpc and create vpc peering.



Click to create peering connection.


Now go the Action and accept the peering connection.


Now go the ec2 machine and change the vpc-peering machine security .

Add rule VPC-PEERING1 IPv4.

Now go the ec2 machine and change the VPC-PEERING1 machine security.

Add rule vpc-peering IPv4.

Now go to the route table and edit vpc1-route-table and add VPC2-ROUTE-TABLE.


Now go to the route table, edit VPC2-ROUTE-TABLE and add vpc-route-table.

Now you can see peering connection is done.