AWS Basics:
Amazon Web Services (AWS) is a cloud computing platform offered by Amazon.com. It provides a wide range of services, including computing power, storage options, networking, databases, machine learning, and more, all delivered over the internet. AWS allows businesses and individuals to access scalable and reliable computing resources without the need to invest in costly infrastructure.
One of the key features of AWS is its scalability. Users can easily scale their resources up or down based on demand, allowing them to accommodate fluctuating workloads without over-provisioning or experiencing downtime. This scalability is made possible by AWS's pay-as-you-go pricing model, where users only pay for the resources they consume, eliminating the need for large upfront investments.
AWS offers a vast array of services to meet the diverse needs of its customers. Some of the core services include:
Amazon Elastic Compute Cloud (EC2): EC2 provides resizable compute capacity in the cloud, allowing users to quickly deploy virtual servers to run their applications.
Amazon Simple Storage Service (S3): S3 offers scalable object storage for data backup, archival, and analytics. It provides high durability, availability, and security for storing and retrieving data.
Amazon Relational Database Service (RDS): RDS simplifies the setup, operation, and scaling of relational databases such as MySQL, PostgreSQL, and SQL Server in the cloud.
Amazon Virtual Private Cloud (VPC): VPC allows users to create isolated virtual networks within the AWS cloud, giving them control over network configuration, IP addressing, and security.
Amazon Lambda: Lambda is a serverless compute service that allows users to run code without provisioning or managing servers. It automatically scales based on incoming requests, making it ideal for event-driven applications and microservices.
Amazon Elastic Load Balancing (ELB): ELB automatically distributes incoming application traffic across multiple targets, such as EC2 instances, to ensure high availability and fault tolerance.
Security is a top priority for AWS, and the platform provides a wide range of tools and features to help users secure their data and applications. These include identity and access management (IAM), encryption, network security, compliance certifications, and more.
IAM Basic:
Identity and Access Management (IAM) is a fundamental component of Amazon Web Services (AWS) that enables users to securely control access to AWS services and resources. IAM allows you to manage users, groups, roles, and permissions, thereby ensuring that only authorized individuals or systems can interact with your AWS environment.
Users, Groups, and Roles:
Users: IAM users are entities with unique credentials (username and password or access keys) used to access AWS services and resources. Each user has its own security credentials and access permissions, which can be managed centrally through IAM.
Groups: IAM groups are collections of users with similar access requirements. Instead of assigning permissions to individual users, you can assign permissions to groups, making it easier to manage access across multiple users with similar roles.
Roles: IAM roles are sets of permissions that define what actions an entity (such as an IAM user, AWS service, or external identity) can perform. Roles are often used to grant temporary access to AWS services or resources and are associated with policies that define the specific permissions.
Key Concepts:
Policies: IAM policies are JSON documents that define permissions and access controls. Policies can be attached to users, groups, roles, or even directly to AWS resources. They specify what actions are allowed or denied and on which resources.
Access Control Lists (ACLs): ACLs are used to control access to individual AWS resources, such as S3 buckets or SQS queues. They provide fine-grained control over who can access the resource and what actions they can perform.
Multi-Factor Authentication (MFA): MFA adds an extra layer of security to user authentication by requiring users to provide two or more forms of verification (e.g., password and temporary code from a physical device or mobile app).
Identity Federation: IAM supports identity federation, allowing users to access AWS resources using existing credentials from corporate directories (such as Active Directory) or third-party identity providers (such as Google or Facebook).
Best Practices:
Principle of Least Privilege: Grant only the permissions necessary for users to perform their tasks. Avoid granting excessive permissions that could lead to misuse or compromise.
Regular Review: Periodically review IAM policies, roles, and user permissions to ensure they align with current business requirements and security policies.
Use IAM Roles for AWS Resources: Instead of hardcoding access keys into applications running on EC2 instances, use IAM roles to grant permissions dynamically. This improves security and reduces the risk of accidental exposure of credentials.
Enable MFA: Enforce the use of Multi-Factor Authentication (MFA) for IAM users with administrative privileges to add an extra layer of security.
Monitor IAM Activity: Use AWS CloudTrail to monitor IAM actions and detect any unauthorized or suspicious activity.
IAM plays a critical role in securing your AWS environment, providing granular control over who can access your resources and what actions they can perform. By following IAM best practices and understanding its core concepts, you can effectively manage access and maintain the security of your AWS infrastructure.
AWS EC2 Automation.
Automating AWS EC2 instances is crucial for streamlining deployment, configuration, scaling, and maintenance tasks, ensuring efficient resource utilization and reducing manual effort. Various automation tools and techniques can be leveraged to achieve this goal, such as AWS CloudFormation, AWS Systems Manager, AWS SDKs, and third-party tools like Ansible or Terraform.
AWS CloudFormation:
AWS CloudFormation enables infrastructure as code (IaC) by allowing users to define templates in JSON or YAML format to provision and manage AWS resources. These templates specify the configuration of EC2 instances, including instance type, security groups, key pairs, and user data scripts. CloudFormation ensures consistent deployments and facilitates version control and rollback capabilities.
Example CloudFormation Template:
Resources:
MyEC2Instance:
Type: AWS::EC2::Instance
Properties:
ImageId: ami-12345678
InstanceType: t2.micro
SecurityGroupIds:
- sg-12345678
KeyName: MyKeyPair
UserData:
Fn::Base64: |
#!/bin/bash
apt update
apt install -y apache2
AWS Systems Manager (SSM):
AWS Systems Manager provides a suite of tools for managing EC2 instances at scale, including automation, patch management, and Run Command. Automation documents in Systems Manager enable users to define workflows to perform common tasks, such as instance provisioning, software installation, and configuration management.
Example SSM Automation Document:
{
"schemaVersion": "0.3",
"description": "Install Apache Web Server",
"parameters": {},
"mainSteps": [
{
"action": "aws:runShellScript",
"name": "InstallApache",
"inputs": {
"runCommand": ["#!/bin/bash", "apt update", "apt install -y apache2"]
}
}
]
}
AWS SDKs and CLI:
AWS Software Development Kits (SDKs) and Command Line Interface (CLI) provide programmatic access to AWS services, enabling developers to automate EC2 instance management tasks using scripting languages like Python, JavaScript, or PowerShell. With SDKs and CLI, users can create, start, stop, terminate, and monitor EC2 instances dynamically based on business requirements or events.
Example CLI Command:
aws ec2 run-instances --image-id ami-12345678 --count 1 --instance-type t2.micro --key-name MyKeyPair --security-group-ids sg-12345678 --user-data file://userdata.sh
Third-party Tools:
Tools like Ansible, Terraform, and Puppet provide additional capabilities for EC2 automation, offering declarative configuration management, infrastructure provisioning, and orchestration across hybrid or multi-cloud environments. These tools abstract the underlying APIs and provide higher-level abstractions for managing infrastructure as code.
Example Ansible Playbook:
- name: Install Apache Web Server
hosts: myec2instance
tasks:
- name: Update apt package index
apt:
update_cache: yes
- name: Install Apache2
apt:
name: apache2
state: present
By leveraging automation tools like CloudFormation, Systems Manager, SDKs, and third-party solutions, organizations can achieve greater efficiency, agility, and consistency in managing EC2 instances, ultimately improving operational excellence and reducing operational overheads in AWS environments.
Create 3 IAM users of avengers and assign them in devops groups with IAM policy:
First go AWS Account and go to user Section. Create 3 User.
Now First we create First user that is "User1".

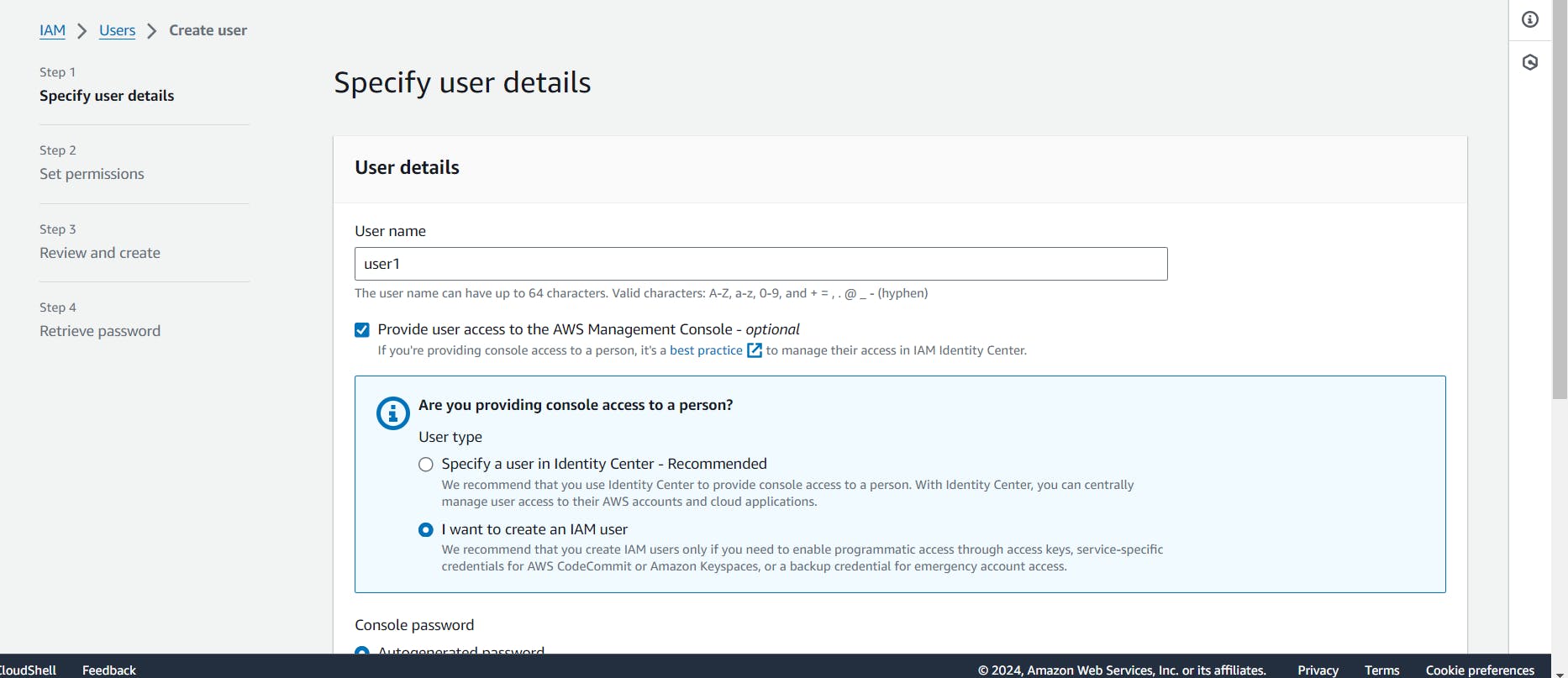
Now you see for user name that is "User1". After that click to chect box that is provide user access to the AWS Management Consol, When you will select this chat box that is provide.

Now IAM provide two types password tha is "Autogenerated Password", "Custom Password". So I have selected "Autogenerated Password" that is means IAM provide me Auto generated password.

After that click to next button. Now When we click next button, Console provide you 3 set of permissions.

The set of permissions you've mentioned refers to three different ways in which access permissions can be managed in IAM (Identity and Access Management) within the AWS (Amazon Web Services) environment:
Add user to group: This permission allows a user to add other IAM users to a specific IAM group. IAM groups are collections of users with similar access requirements, and by adding users to a group, you're effectively granting them the same permissions as the group. This permission is useful for administrators who need to manage user access efficiently by organizing users into logical groups and applying permissions at the group level rather than individually to each user.
Copy permissions: This permission allows a user to copy permissions from one IAM entity (such as a user, group, or role) to another. It enables administrators to replicate or transfer permissions configurations from one entity to another, simplifying the management of access controls. By copying permissions, you can ensure consistency and accuracy in permission assignments across your AWS environment.
Attach policies directly: This permission allows a user to attach IAM policies directly to IAM users, groups, or roles. IAM policies are JSON documents that define permissions and access controls, specifying what actions are allowed or denied on which AWS resources. By attaching policies directly, you can grant specific permissions to individual entities without relying solely on group memberships or role assumptions. This provides flexibility in managing access permissions tailored to the needs of each IAM entity.
Now I have selected Attach policies directly., When I have selected this permissions, It is showing Attached the policies directly.

Now I have provide EC2 Full access policies and IAM Full access policies.
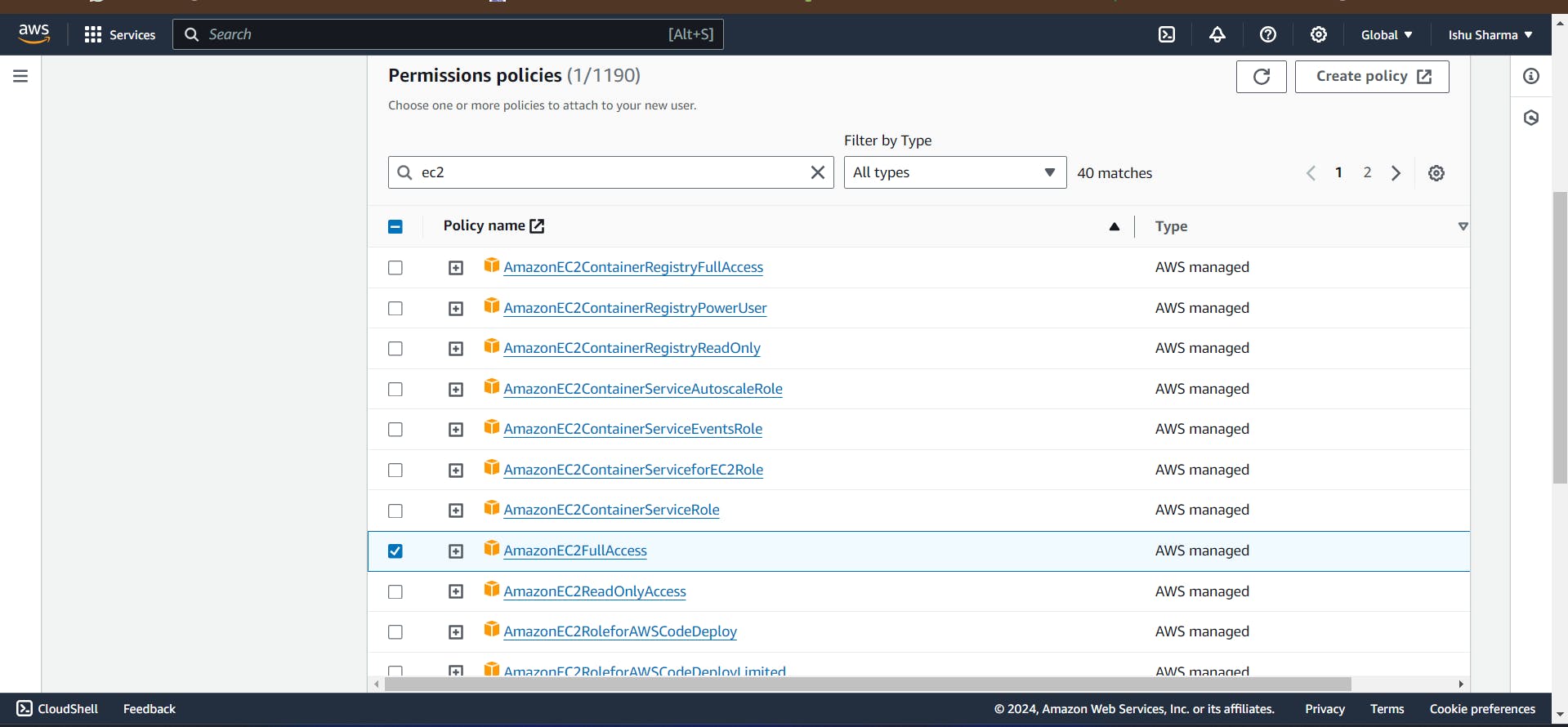
After that click to next button.
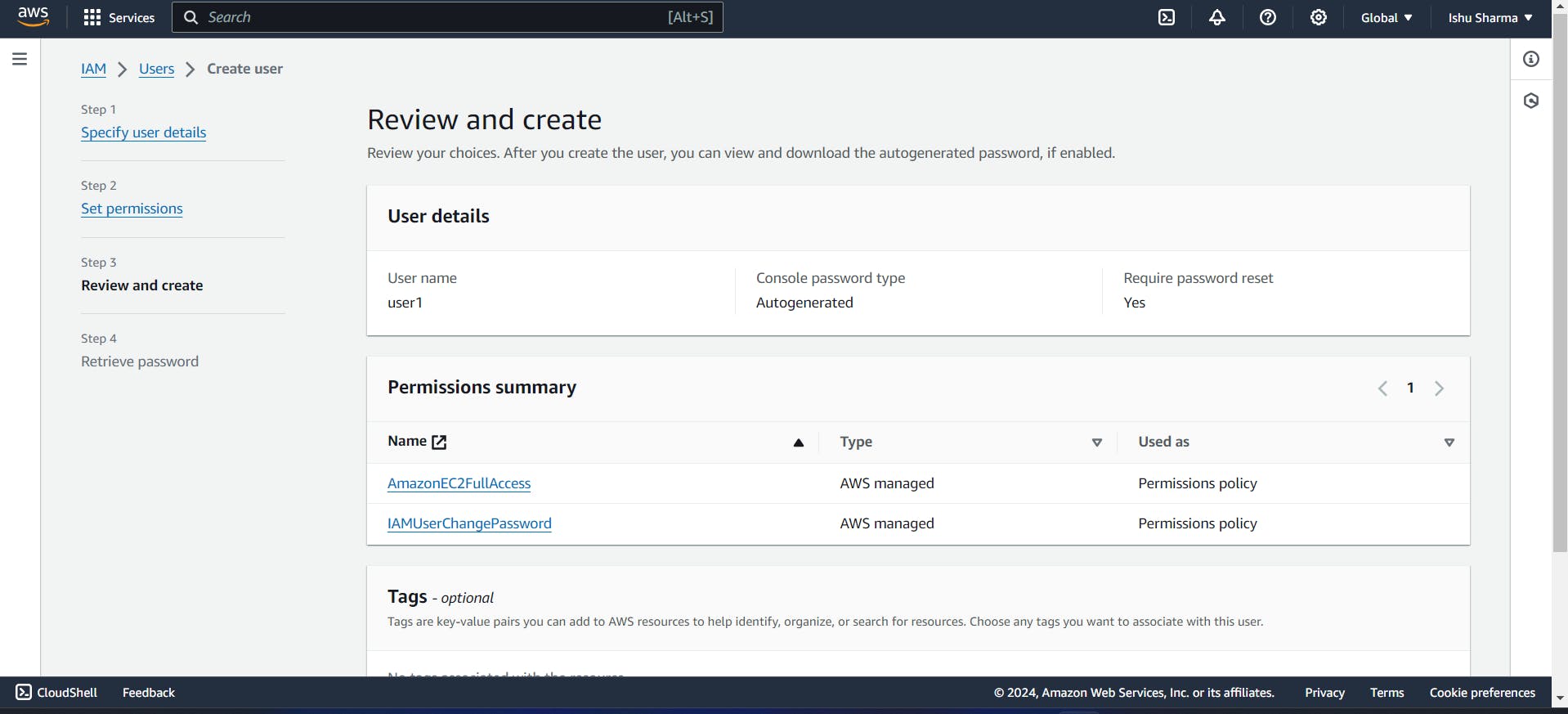

When I click next button, It is sowing that Review and Create that is means you can Review all, Everything is right you can create.

So Now I have selected create user button.

It is showing user created successfully. It means we have created user successfully. Now Click to "Dowload .csv file" it is showing auto generated password after that click to "return to user list".
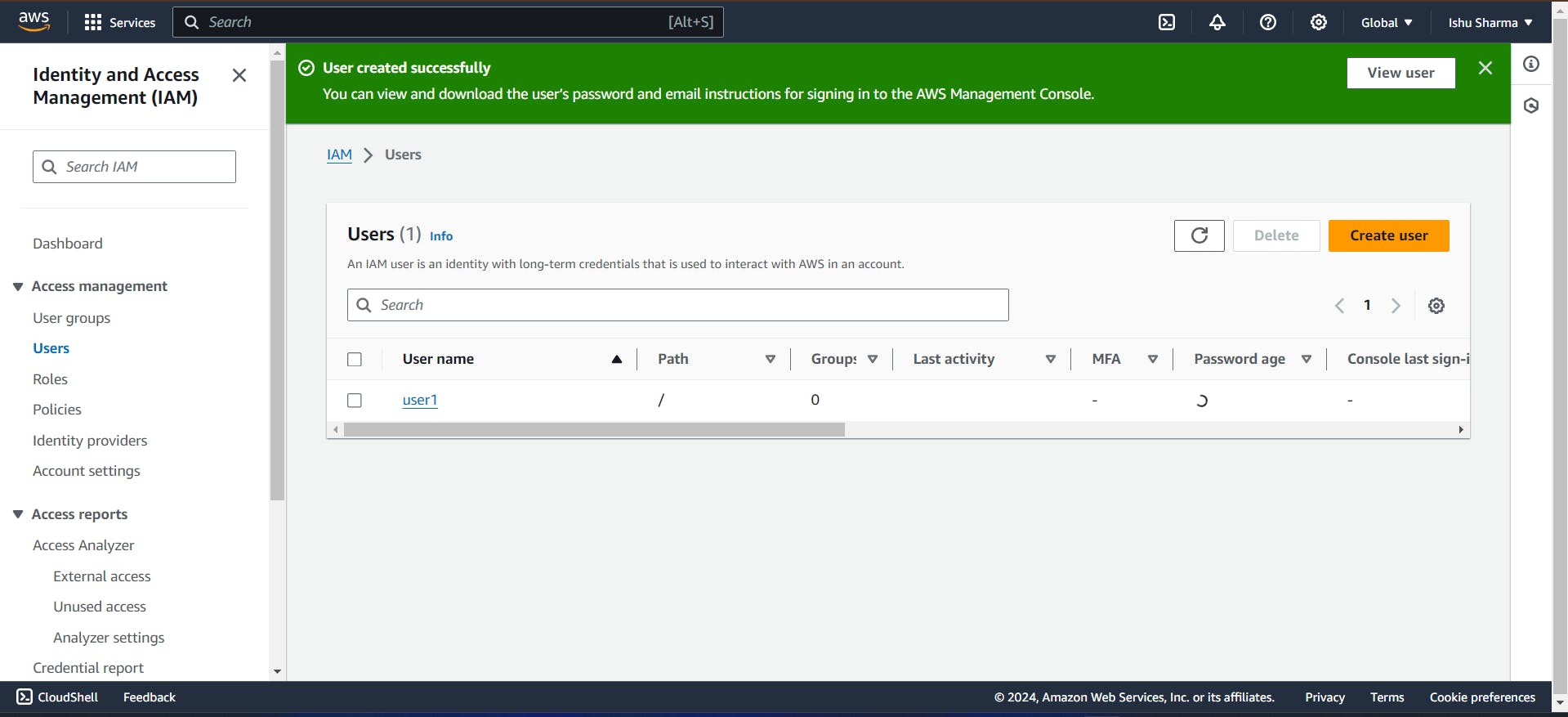
Now, We have created user1, Similarly we need to create user2 and user3.
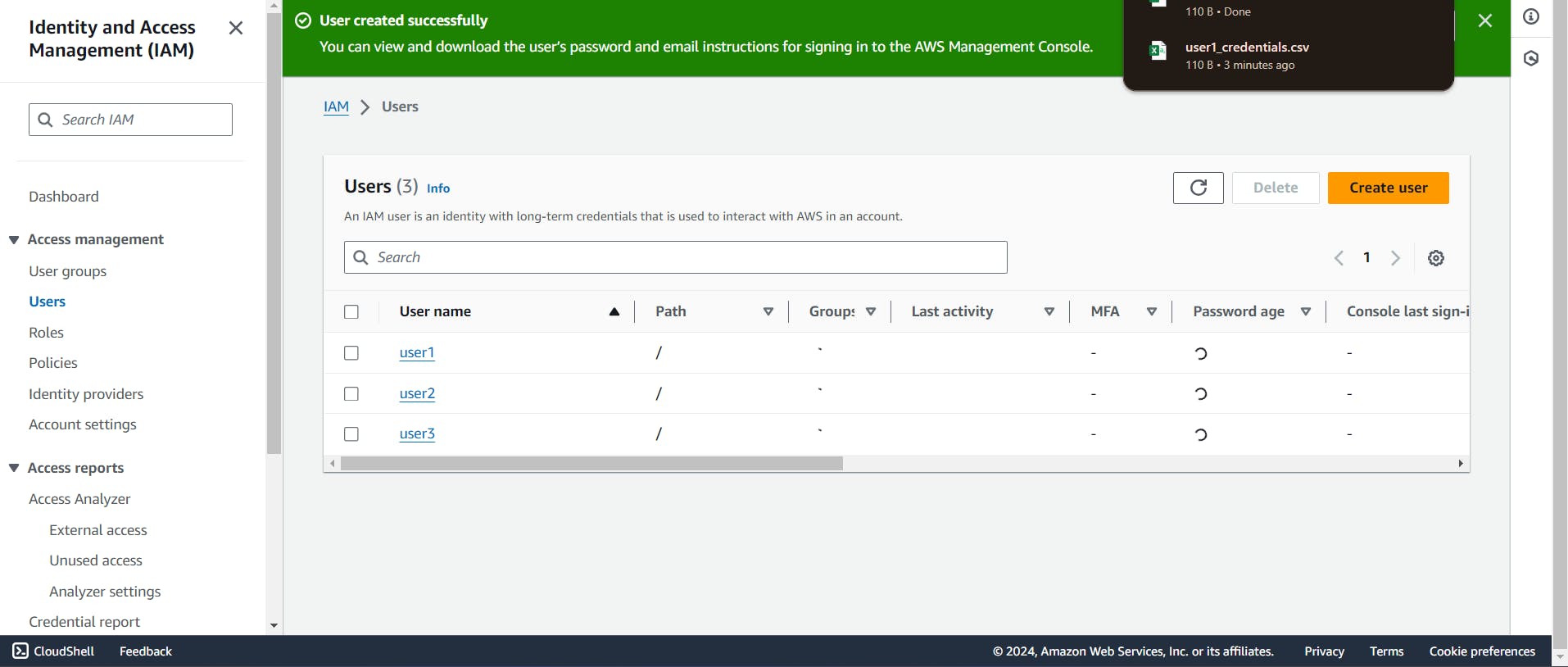
Now, We have created 3 users and provide the similar policies that is "ec2 full access" and "IAM Full Access".
Create the Group and assign the users for this group:
First we need to create Devops name group. So go IAM and select the user groups section.
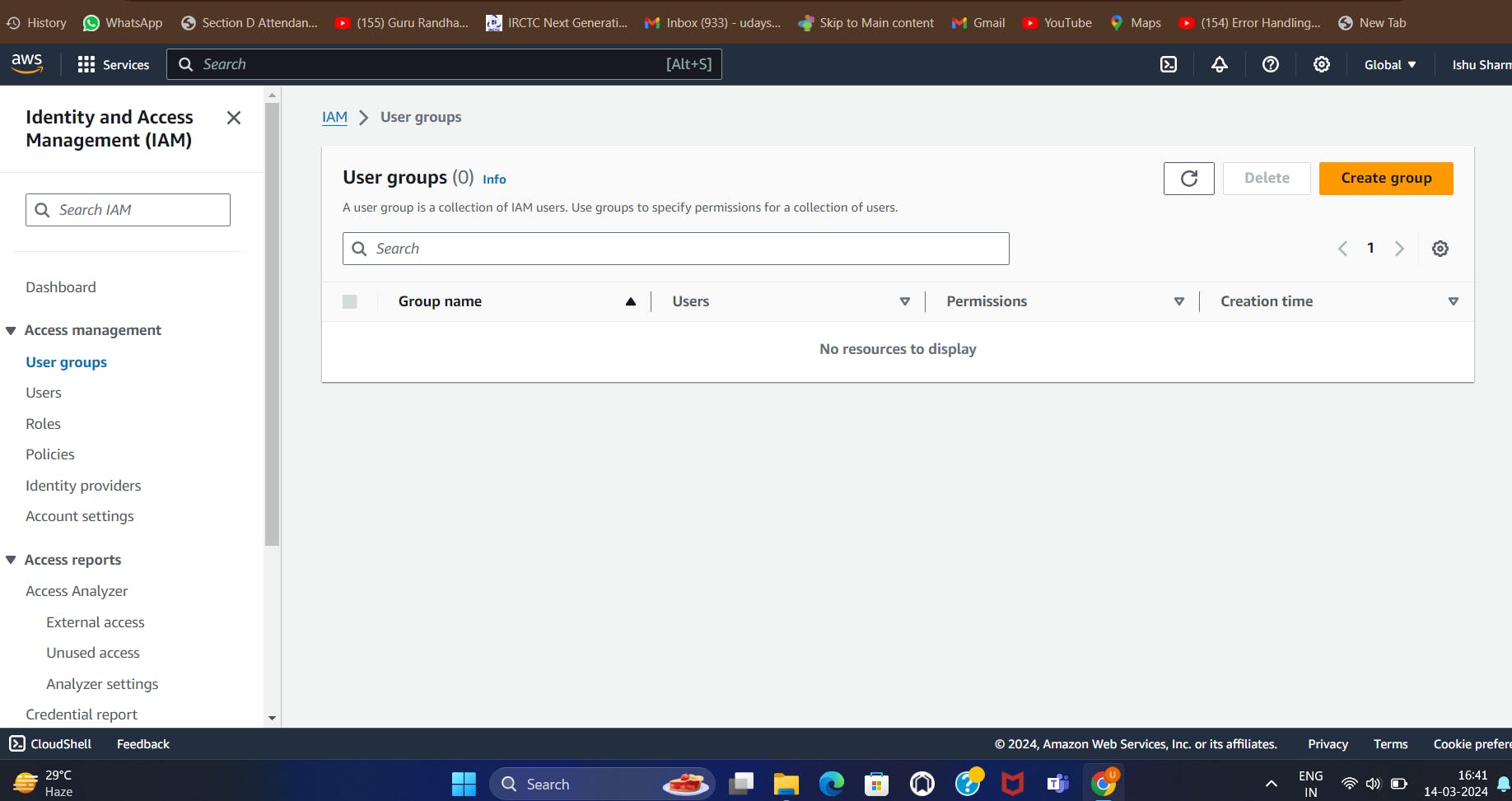
Now, click to "create group " name button.

Now, We need to enter user group name that is devops.

After that go to Add user to the group section and attached all the user and go the the Attach Permissions policies and attach "EC2 Full Access" and "IAM Full Access" Policies after that click to "create group button"

Login to user1:
Now, We have alredy Download .csv file for "user1", So First open this file and it is showing "consol-signin-url", "username" and "password". So we need to login using "consol-signin-url". So copy this url and paste another browser.

Now, It is showing IAM User name and Password . So We need to provide.

After that, Click to sign in button.
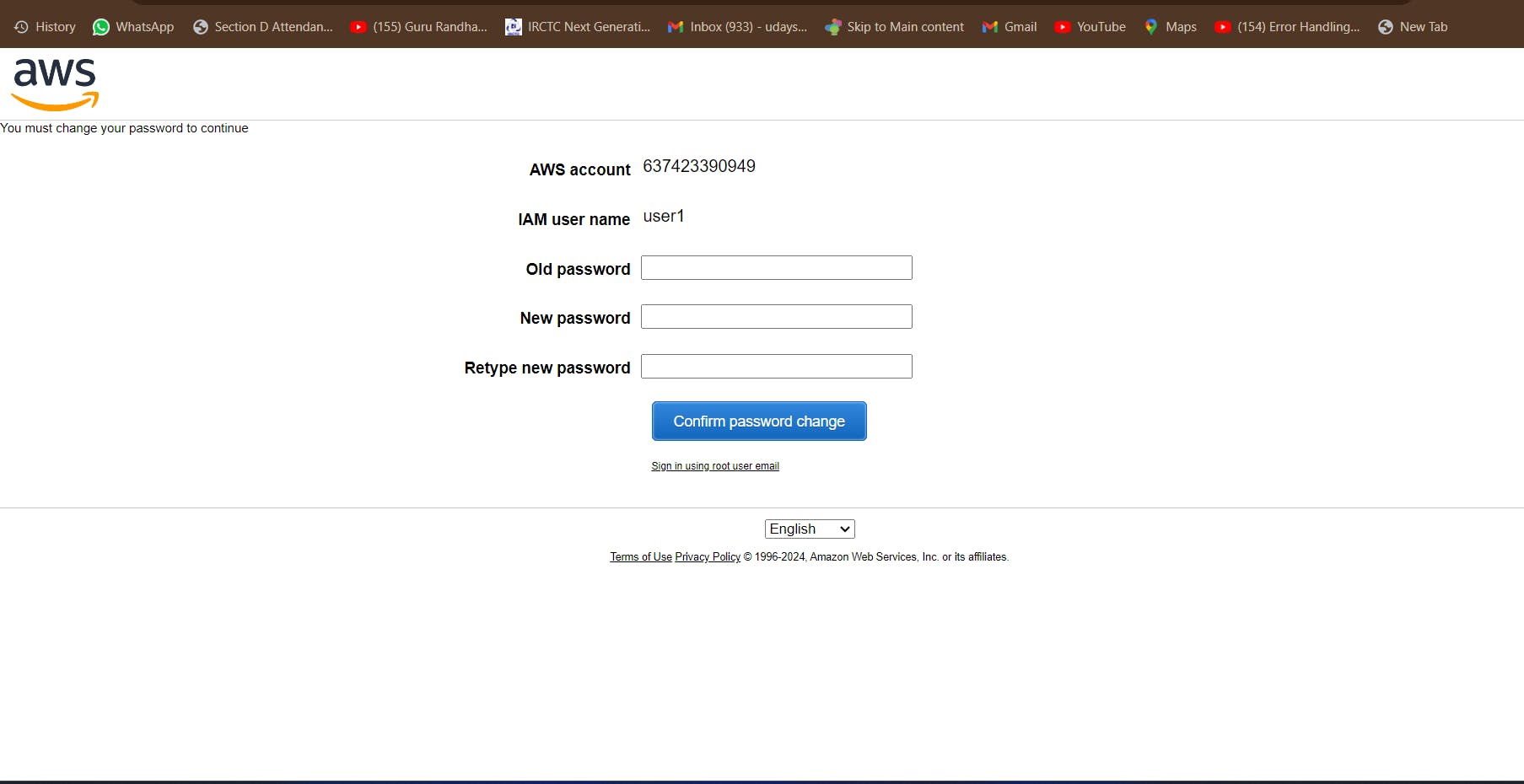
When you click to sign in button it is showing change your password, If you need to change the password. So I need to change the password and after that click to confirm password change button.

Now for this user1 we have only Ec2 Machine Service access. so we can use only one service. we can not user another service.
